When using a Cisco ASA for Remote Access VPN (SSL-VPN or IKEv2/IPSec) with the AnyConnect client, in most typical scenarios ALL traffic from the AnyConnect VPN client is encrypted and tunnelled back to the ASA. When using the ASA as the VPN headend device with the AnyConnect client you can use split tunnelling feature, which can be configured to include or exclude certain networks from the VPN tunnel.
- See All Results For This Question
- Cisco AnyConnect Secure Mobility Client Administrator Guide ..
- Anyconnect Allow Local Lan Access
- Download Cisco AnyConnect VPN Client - File.org - We Help ..
Working on an upcoming project with Cisco Anyconnect. Long story short there will be a couple of tablets with Cisco Anyconnect loaded, and connect back to our network through Verizon's cellular network. During the week some of the tablets will be taken out of their vehicle, and need to connect to our local wifi, and then access its local resources. Start Cisco Anyconnect VPN. From the menu select: Cisco Anyconnect VPN Client Preferences; Check the box next to Enable Local LAN access (if configured). Your settings changes will not take effect until the next time you start the VPN client. Quit the VPN client. Restart Cisco Anyconnect VPN and connect to the MIT VPN.
See All Results For This Question
The basic configuration of a Remote Access VPN to tunnel all traffic back to the ASA
On Windows the AnyConnect Route Details would indicate 0.0.0.0/0 is a Secured Route, meaning all traffic is tunnelled back to the ASA.
The native Windows IKEv2 client does not support split tunnelling, so the only possible configuration with the Microsoft client is to tunnel all traffic (split-tunnel-policy tunnelall).
Split Tunnel (tunnelspecified)
In certain circumstances tunnelling all traffic back to the ASA may not be desirable; split tunnelling can be configured to tunnel specific networks over the VPN. An ACL must be created defining which networks should be routed over the tunnel and the group policy should be modified to change the split-tunnel-policy to tunnelspecified and adding the command split-tunnel-network-list.
On Windows, the AnyConnect Route Details now displays the tunnelled networks (192.168.10.0/24 and 192.168.9.0/24) as specified in the ACL. The reason the 2 /32 networks appear is because those IP addresses were defined in the group-policy as the DNS servers.
Split Tunnel Exclude (excludedspecified)

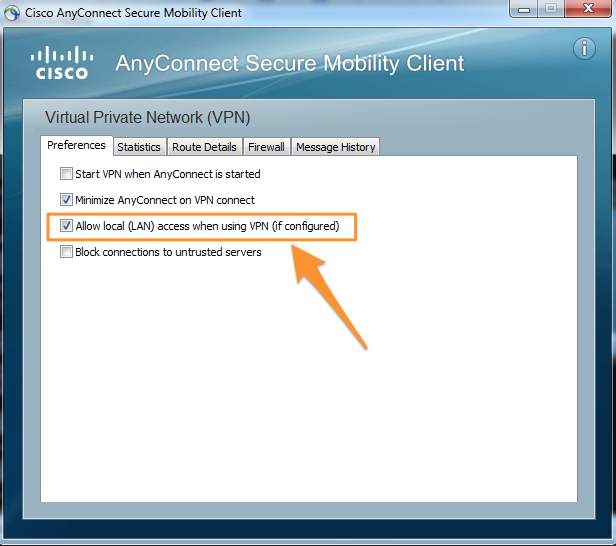
Another option is to tunnel all traffic except a list specified, the AnyConnect Client must be configured to permit this, as by default this is disabled. This can be enabled by the user in the AnyConnect Client via the Preferences tab > Allow local (LAN) access when using VPN (if configured) option.
An administrator can also configure this in the AnyConnect XML configuration file modifying the file directly <LocalLanAccess UserControllable=”true”>true</LocalLanAccess>
and change false to true. Alternatively this can be configured via the AnyConnect VPN Profile Editor.
Configure the ACL for networks to be excluded from the VPN tunnel
Re-configure the Group Policy, changing the Policy to excludespecified and specifying the Network List
Re-connecting to the VPN tunnel, the Route Details tab in the AnyConnect client will confirm the networks not routed via the VPN tunnel.
Split Tunnel Exclude + Allow Local LAN
The AnyConnect VPN client can be configured to permit access to the local LAN network, in order to access local resources such as a local network printer or NAS. This relies on the configuration for excludespecified as above.
Modify the ACL (created above for Split Tunnel Exclude) in order to allow local LAN access
Re-connecting to the VPN tunnel, the routing table of the Windows client will now have the local network (10.20.0.0/24) in the Non-Secured Routes (IPv4).
You should now be able to ping the local LAN network, in this example 10.20.0.0/24
When using a Cisco ASA for Remote Access VPN (SSL-VPN or IKEv2/IPSec) with the AnyConnect client, in most typical scenarios ALL traffic from the AnyConnect VPN client is encrypted and tunnelled back to the ASA. When using the ASA as the VPN headend device with the AnyConnect client you can use split tunnelling feature, which can be configured to include or exclude certain networks from the VPN tunnel.

The basic configuration of a Remote Access VPN to tunnel all traffic back to the ASA
Battle vs chess mac download.
On Windows the AnyConnect Route Details would indicate 0.0.0.0/0 is a Secured Route, meaning all traffic is tunnelled back to the ASA.
The native Windows IKEv2 client does not support split tunnelling, so the only possible configuration with the Microsoft client is to tunnel all traffic (split-tunnel-policy tunnelall).
Split Tunnel (tunnelspecified)
In certain circumstances tunnelling all traffic back to the ASA may not be desirable; split tunnelling can be configured to tunnel specific networks over the VPN. An ACL must be created defining which networks should be routed over the tunnel and the group policy should be modified to change the split-tunnel-policy to tunnelspecified and adding the command split-tunnel-network-list.
Cisco AnyConnect Secure Mobility Client Administrator Guide ..
On Windows, the AnyConnect Route Details now displays the tunnelled networks (192.168.10.0/24 and 192.168.9.0/24) as specified in the ACL. The reason the 2 /32 networks appear is because those IP addresses were defined in the group-policy as the DNS servers.
Split Tunnel Exclude (excludedspecified)
Another option is to tunnel all traffic except a list specified, the AnyConnect Client must be configured to permit this, as by default this is disabled. This can be enabled by the user in the AnyConnect Client via the Preferences tab > Allow local (LAN) access when using VPN (if configured) option.
An administrator can also configure this in the AnyConnect XML configuration file modifying the file directly <LocalLanAccess UserControllable=”true”>true</LocalLanAccess>
and change false to true. Alternatively this can be configured via the AnyConnect VPN Profile Editor.
Configure the ACL for networks to be excluded from the VPN tunnel
Re-configure the Group Policy, changing the Policy to excludespecified and specifying the Network List
Re-connecting to the VPN tunnel, the Route Details tab in the AnyConnect client will confirm the networks not routed via the VPN tunnel.
Split Tunnel Exclude + Allow Local LAN
The AnyConnect VPN client can be configured to permit access to the local LAN network, in order to access local resources such as a local network printer or NAS. This relies on the configuration for excludespecified as above.
Modify the ACL (created above for Split Tunnel Exclude) in order to allow local LAN access
Re-connecting to the VPN tunnel, the routing table of the Windows client will now have the local network (10.20.0.0/24) in the Non-Secured Routes (IPv4).
Download keka mac.
Anyconnect Allow Local Lan Access
You should now be able to ping the local LAN network, in this example 10.20.0.0/24
Download Cisco AnyConnect VPN Client - File.org - We Help ..
